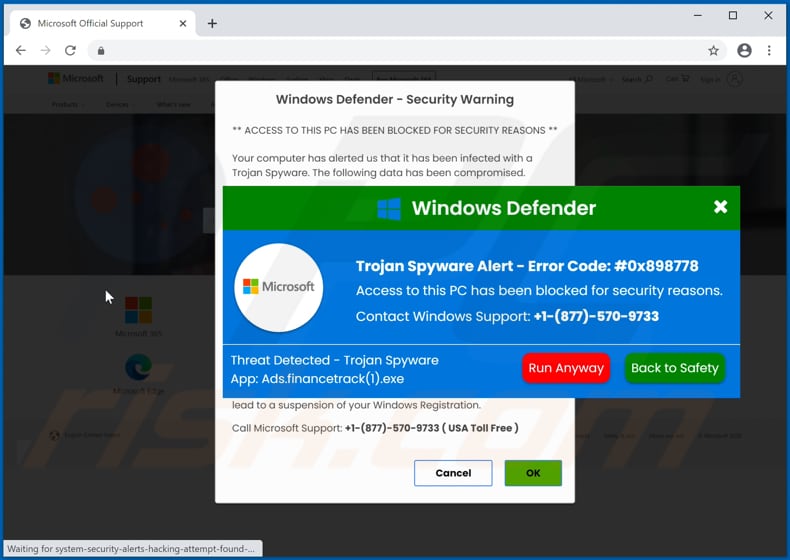
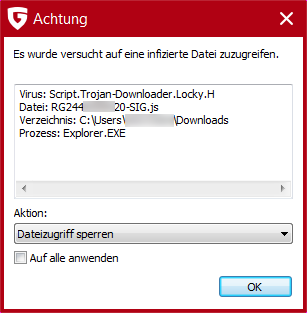
What is a Trojan horse attack Shiksha Online top, What is Proxy Trojan GeeksforGeeks top, What Is a Trojan a Virus or Malware How Does It Work Avast top, Cross platform Trojan controls Windows and Mac machines top, Your System Has Been Hacked With A Trojan Virus Email Scam top, What is a Trojan Horse Virus Definition Examples Removal top, What are Banking Trojans GeeksforGeeks top, What is a Trojan horse attack Shiksha Online top, Trojan PowerPoint Presentation and Slides SlideTeam top, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus top, What is Trojan Horse Computing zenarmor top, What is a Trojan Horse Virus Types Prevention in 2024 top, 17 Ransomware Examples How They Occurred UpGuard top, Encryption Trojan Locky What you need to know about the ransomware top, Trojan Spyware Alert POP UP Scam Removal and recovery steps top, What is Proxy Trojan GeeksforGeeks top, What is a Trojan Virus Trojan Horse Virus Box Inc top, What is Trojan Horse Malware and how can you avoid it top, What Is a Trojan Virus Definition Types Prevention Tips top, What is a Trojan Horse Virus Definition Examples Removal Options Video top, What Are Trojans How Can You Protect Yourself top, Different Examples of a Trojan Horse Types of Trojan Horse top, Placeholder Trojan Writing a Malware Software top, Remote Access Trojan RAT Malware Signs How to Detect top, What Is a Trojan Horse in Computer Terms InfoSec Insights top, How trojan malware is evolving to survive and evade cybersecurity top, Trojan Horse Virus Examples How to Defend Yourself top, Types of Trojan Attacks 2015. Network Browser Exploits and top, Example of Trojan malware propagation in online social networks top, What Is a Trojan a Virus or Malware How Does It Work Avast top, What is a Trojan Horse Virus Types Prevention in 2024 top, Placeholder Trojan Writing a Malware Software top, What is a Trojan Virus Trojan Horse Malware Imperva top, Trojan Horse Meaning Examples Prevention top, Trojan Horse Meaning Examples Prevention top, Product Info: Trojan examples top
.
Trojan examples top